Security researchers have come out yet again to show how some of the most downloaded Android apps are lax, when dealing with sensitive private information. Android apps downloaded by as many as 185 million users across the world are vulnerable to hacks, which in turn could reveal users’ online banking, social networking credentials, e-mail and instant-messaging contents and more, reports Ars Technica.
According to researchers from Leibniz University of Hannover, Germany and Philipps University of Marburg, Germany, their manual security audit of some 100 popular free apps revealed widespread and serious vulnerabilities. They were able to capture credentials for American Express, Diners Club, Paypal, Facebook, Twitter, Google, Yahoo, Microsoft Live ID, Box, WordPress, IBM Sametime, remote servers, bank accounts and email accounts.
The security paper released by the researchers does not reveal these vulnerable apps, but stated that they are some of the most popular free apps.
How did they do it?
“Man-in-the-middle” attack, they created a fake Wi-Fi hotspot and used a specially created attack tool to spy on the data the apps sent via that route.
In the researchers’ words:
We used a Samsung Galaxy Nexus smartphone with Android 4.0 Ice Cream Sandwich. We installed the potentially vulnerable apps on the phone and set up a Wi-Fi access point with a MITM SSL proxy. Depending on the vulnerability to be examined, we equipped the SSL proxy either with a self-signed certificate or with one that was signed by a trusted CA, but for an unrelated hostname.
Of the 100 apps selected for manual audit, 41 apps proved to have exploitable vulnerabilities.
Here are some of the example vulnerabilities:
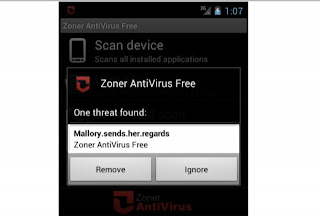
An anti-virus app that accepted invalid certificates when validating the connection supplying new malware signatures. By exploiting that trust, the researchers were able to feed the app their own malicious signature. (see image)
An app with an install base of 1 million to 5 million users that was billed as a “simple and secure” way to upload and download cloud-based data that exposed login credentials. The leakage was the result of a “broken SSL channel.”
A client app for a popular Web 2.0 site with up to 1 million users, which appears to be offered by a third-party developer. It leaked Facebook and Google credentials when logging in to those sites.
A “very popular cross-platform messaging service” with an install base of 10 million to 50 million users exposed telephone numbers from the address book.
Here is their conclusion:
In this paper, we presented an investigation of the current state of SSL/TLS usage in Android and the security threats posed by benign Android apps that communicate over the Internet using SSL/TLS. We have built MalloDroid, a tool that uses static code analysis to detect apps that potentially use SSL/TLS inadequately or incorrectly and thus are potentially vulnerable to MITM attacks. Our analysis of the 13,500 most popular free apps from the Google Play Market has shown that 1,074 apps contain code belonging to this category. These 1,074 apps represent 17.0% of the apps that contain HTTPS URLs. To evaluate the real threat of such potential vulnerabilities, we have manually mounted MITM attacks against 100 selected apps from that set. This manual audit has revealed widespread and serious vulnerabilities. We have captured credentials for American Express, Diners Club, Paypal, Facebook, Twitter, Google, Yahoo, Microsoft Live ID, Box, WordPress, IBM Sametime, remote servers, bank accounts and email accounts. We have successfully manipulated virus signatures downloaded via the automatic update functionality of an anti-virus app to neutralize the protection or even to remove arbitrary apps, including the anti-virus program itself. It was possible to remotely inject and execute code in an app created by a vulnerable app-building framework. The cumulative number of installs of apps with confirmed vulnerabilities against MITM attacks is between 39.5 and 185 million users, according to Google’s Play Market.
The results of our online survey with 754 participants showed that there is some confusion among Android users as to which security indicators are indicative of a secure connection, and about half of the participants could not judge the security state of a browser session correctly. We discussed possible countermeasures that could alleviate the problems of unencrypted traffic and SSL misuse. We over MalloDroid as a rst countermeasure to possibly identify potentially vulnerable apps. The findings of our investigation suggest several areas of future work. We intend to provide a MalloDroid Web App and will make it available to Android users. Moreover, there seems to be a need for more education and simpler tools to enable easy and secure development of Android apps. But most importantly, research is needed to study which countermeasures offer the right combination of usability for developers and users, benefits and economic incentives to be deployed on a large scale.
Read the full research paper here.
No comments:
Post a Comment